Introduction:
The Cisco ASA firewall can be challenging to work with, and using the CLI can be difficult. However, basic configuration can still be done using the ASDM GUI. Since I don’t have a lot of time and energy to research the Cisco ASA firewall in-depth, I’m documenting the setup steps to avoid having to start from scratch again after a long time.
In this example, we will configure NAT (Port Forwarding) for three NVR (CCTV recorders) on the Cisco ASA 5512-X firewall to allow access from the outside network. Details are shown in the following diagram.
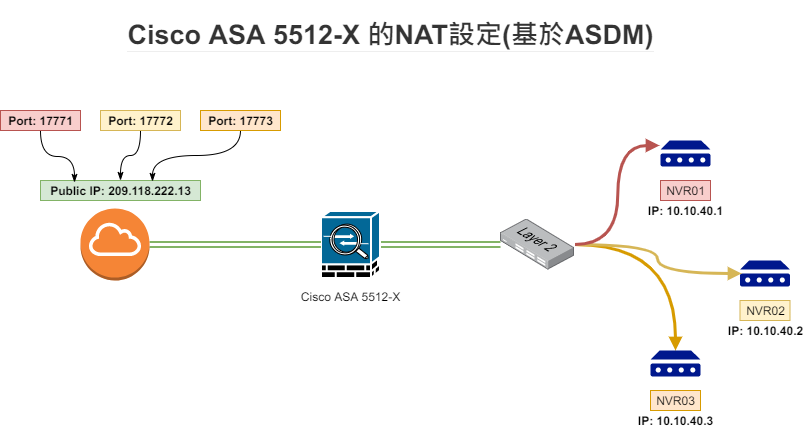
Configuration Example:
Screenshots with minimal annotations.
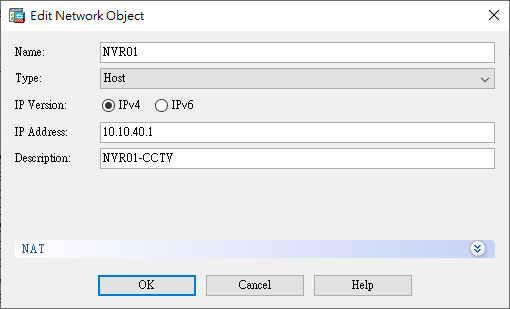
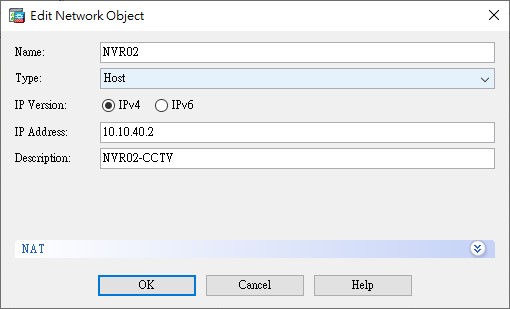
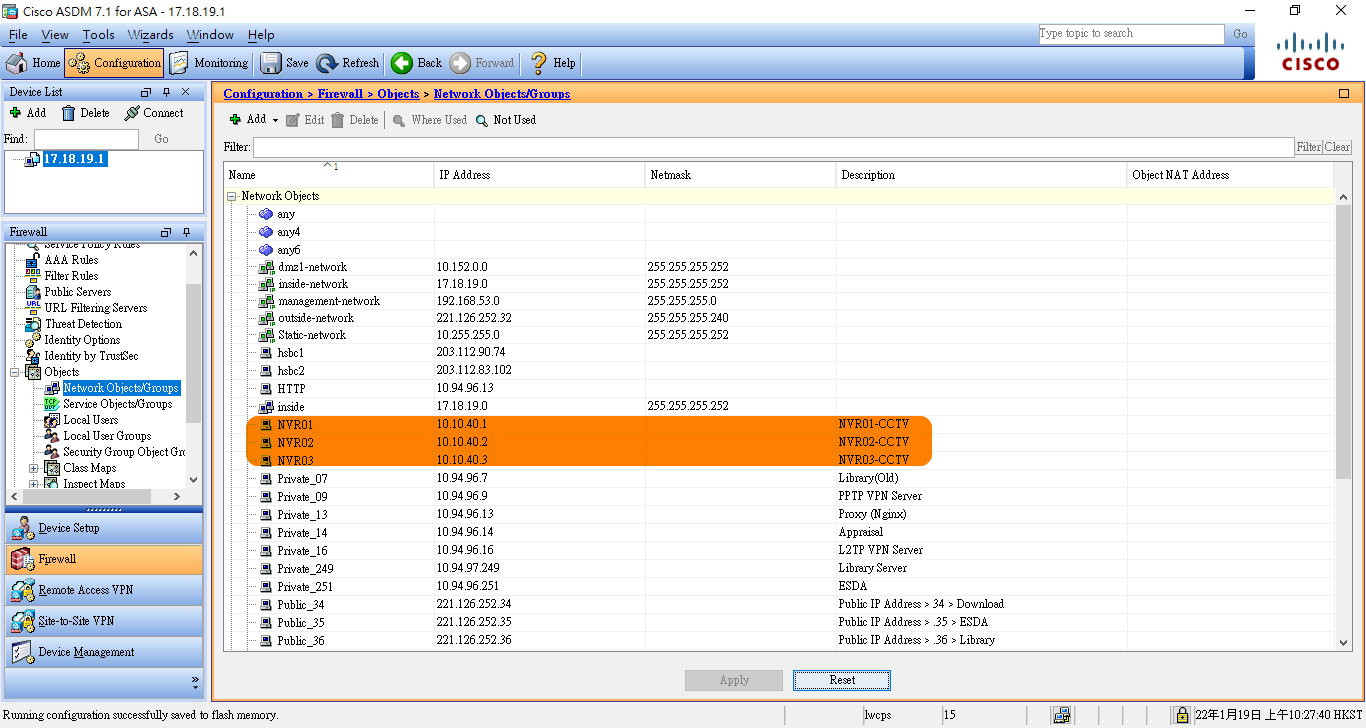
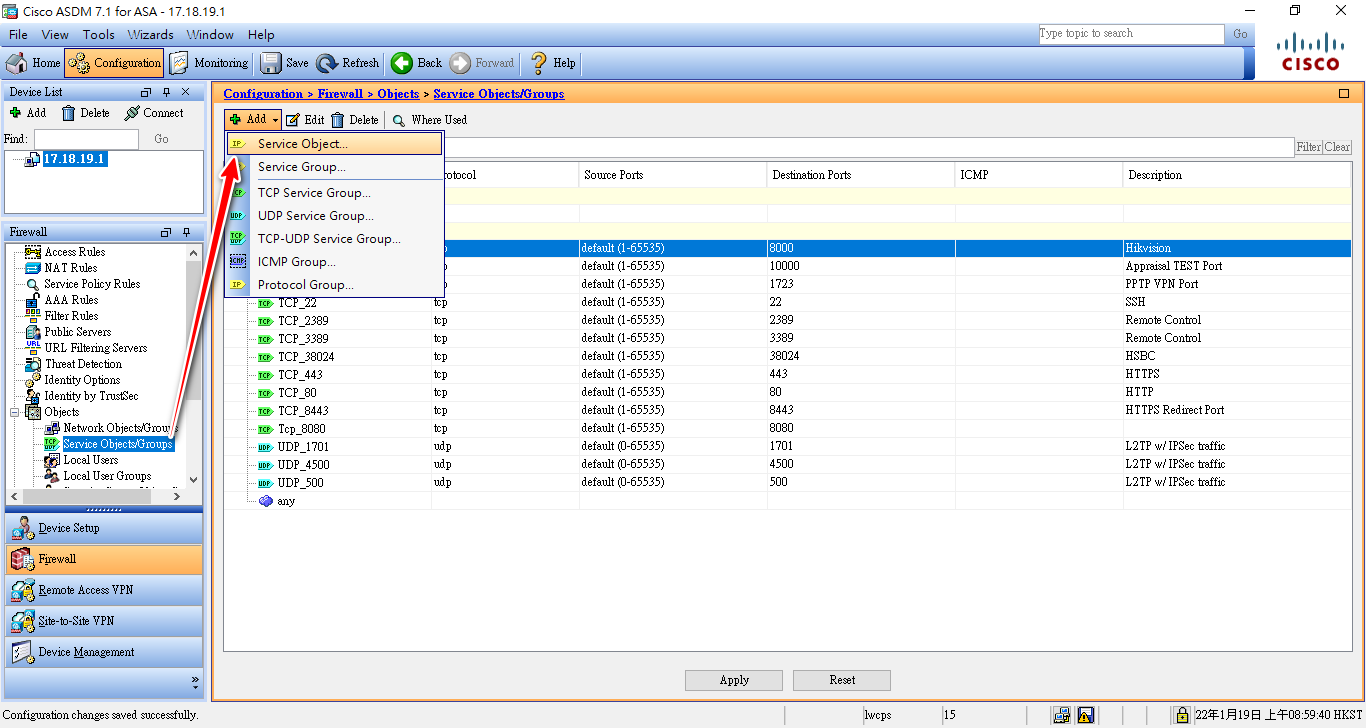
Objects
- Network Objects (Creating network objects)


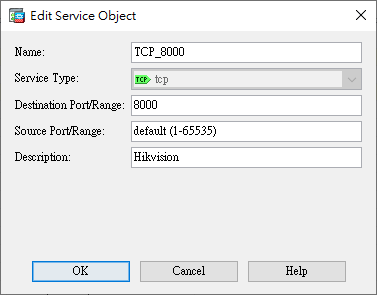
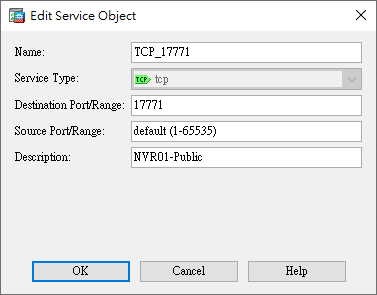
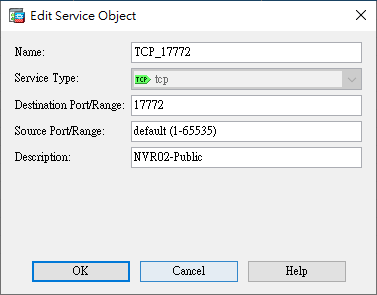
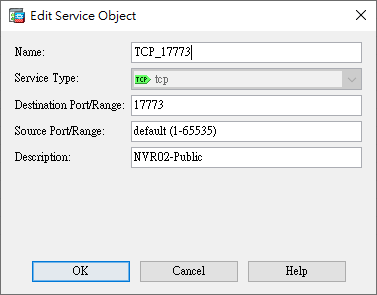
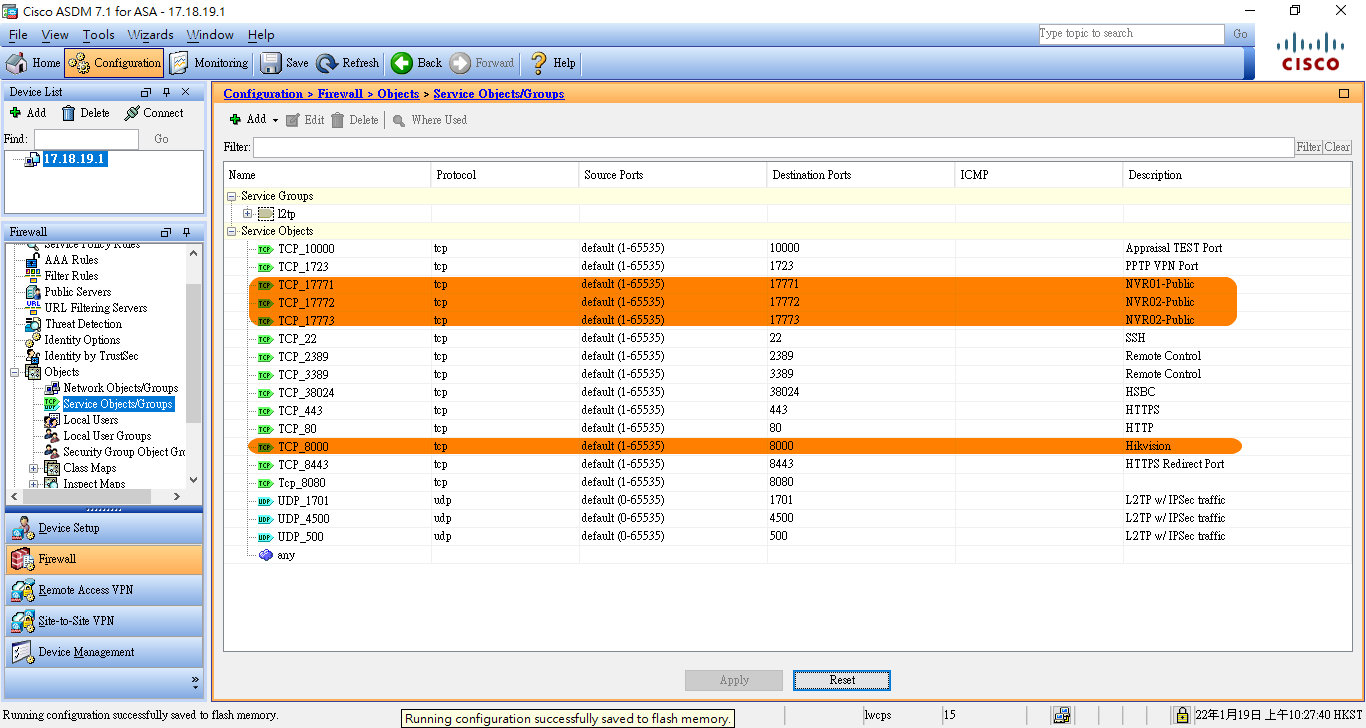
- Service Objects (Creating service objects)
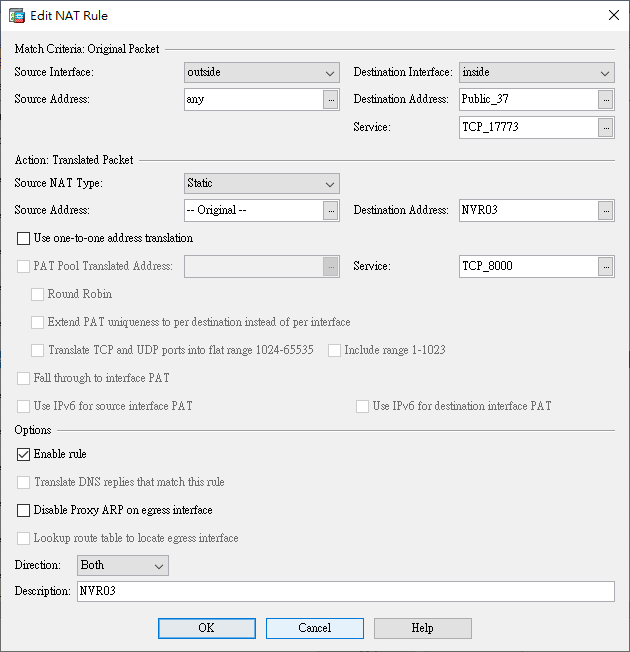
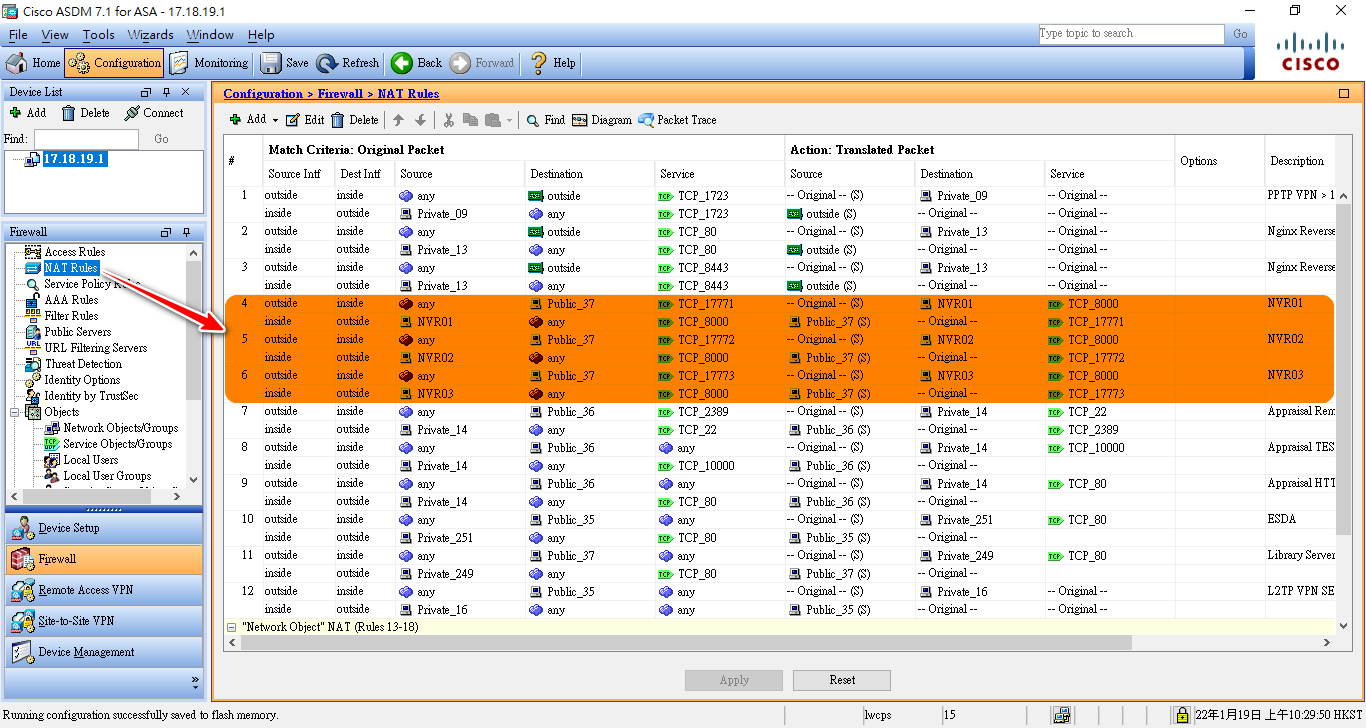
NAT Rules
Creating NAT rules using
Objects.
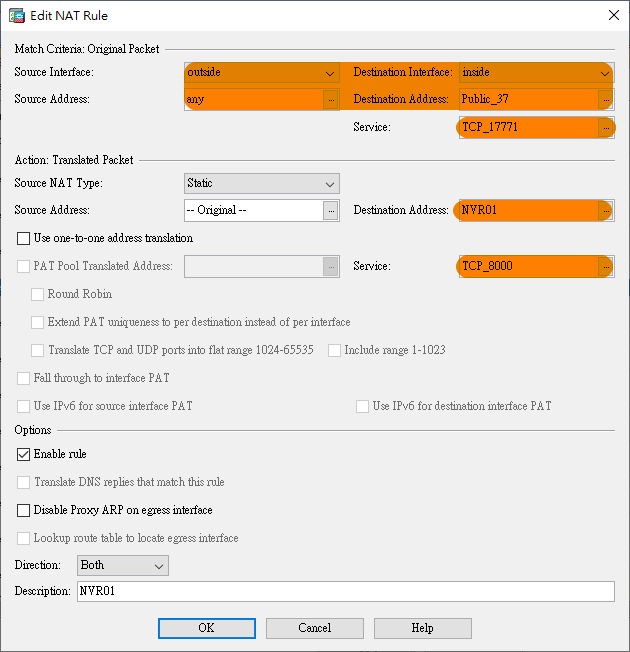
Public_37 (Network Object) is the previously created Public IP address 209.118.222.13.

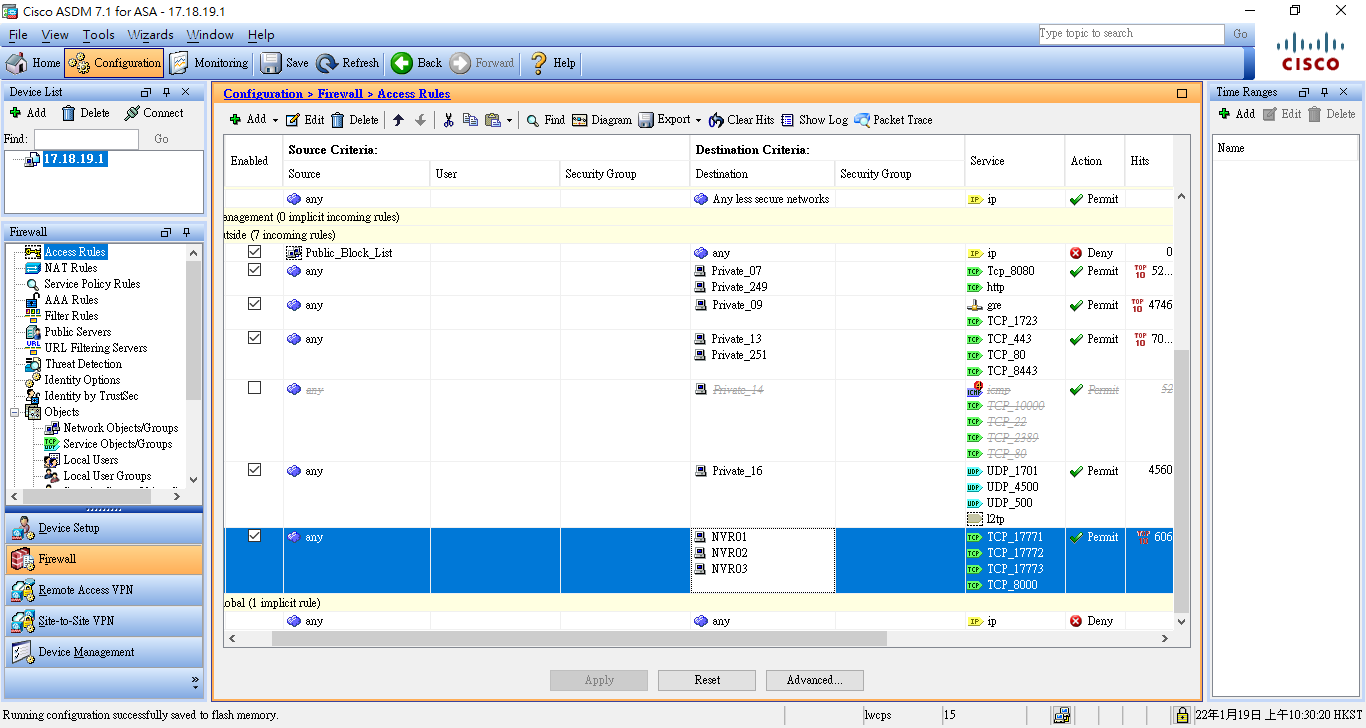
Access Rules
Access rules are necessary to allow access from the outside network to the internal devices.
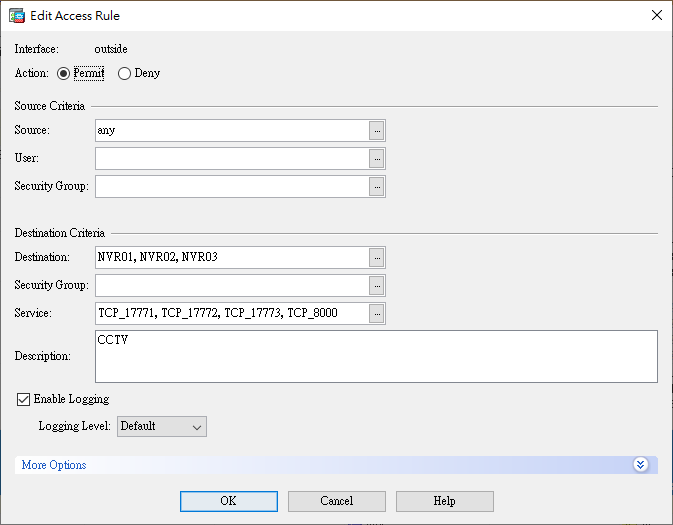
Conclusion:
This example covers the basic configuration of the ASA firewall, with a focus on understanding the basic relationship between
Objects,NAT, andAccess Rules. This will make it easier to configure firewalls from different vendors in the future.
